반응형
gossm 설치 및 사용하기
gossm은 AWS Systems Manger Session Manager와 관련된 대화형 CLI 도구입니다.
전제 조건(Prerequisite)
- ec2
- [required] aws의 ec2 서버에는 aws ssm 에이전트가 설치되어 있습니다.
- [required] ec2 서버는 AmazonSSMManagedInstanceCore iam 정책을 연결해야 합니다.
- ssh를 사용하려면 gossm을 사용하는 scp 명령을 사용하려면 ec2에 aws ssm 에이전트 버전 2.3.672.0 이상이 설치되어 있어야 합니다.
- 사용자
- [required] aws access key, aws secret key
- [required] ec2:DescribeInstances, ssm:StartSession, ssm:TerminateSession, ssm:DescribeSessions, ssm:DescribeInstanceInformation, ssm:DescribeInstanceProperties, ssm:GetConnectionStatus
- [optional] ec2:DescribeRegions에 대한 추가 권한을 얻는 것이 좋습니다.
gossm 다운로드(https://github.com/gjbae1212/gossm/releases)
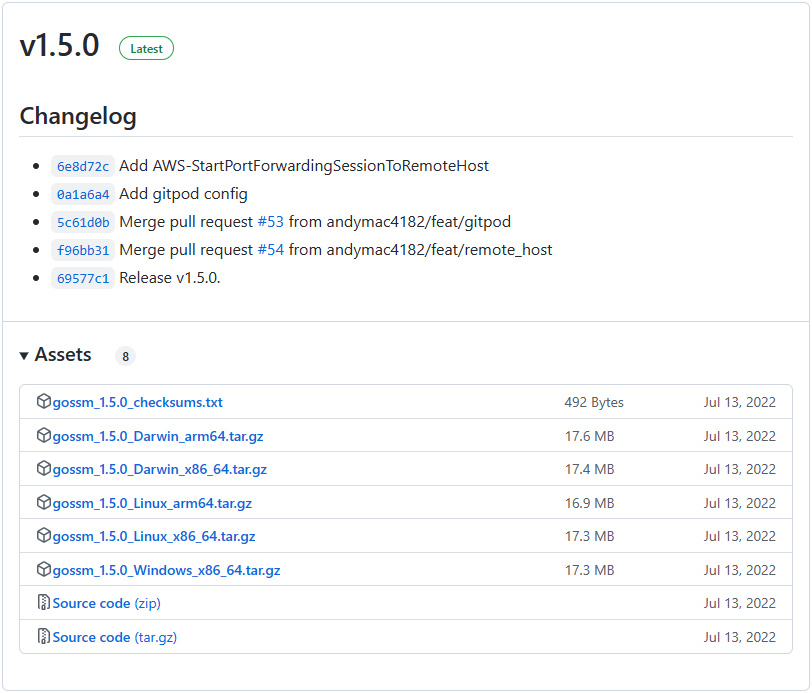
원도우(원도우 11)
다운로드한 gossm 파일을 압축 풀고 환경변수에 PATH 등록합니다.
gossm --version>gossm --version
gossm version v1.5.0mac(bomebrew)
brew tap gjbae1212/gossmbrew install gossm> gossm --version
gossm version v1.5.0> brew upgrade gossm
Warning: gjbae1212/gossm/gossm 1.5.0 already installedgossm 사용법
>gossm --help
gossm is interactive CLI tool that you select server in AWS and then could connect or send files your AWS server using start-session, ssh, scp in AWS Systems Manger Session Manager.
Usage:
gossm [command]
Available Commands:
cmd Exec `run command` under AWS SSM with interactive CLI
completion Generate the autocompletion script for the specified shell
fwd Exec `fwd` under AWS SSM with interactive CLI
fwdrem Exec `fwdrem` under AWS SSM with interactive CLI
help Help about any command
mfa It's to authenticate MFA on AWS, and save authenticated mfa token in .aws/credentials_mfa.
scp Exec `scp` under AWS SSM with interactive CLI
ssh Exec `ssh` under AWS SSM with interactive CLI
start Exec `start-session` under AWS SSM with interactive CLI
Flags:
-h, --help help for gossm
-p, --profile string [optional] if you are having multiple aws profiles, it is one of profiles (default is AWS_PROFILE environment variable or default)
-r, --region string [optional] it is region in AWS that would like to do something
-v, --version version for gossm
Use "gossm [command] --help" for more information about a command.728x90
gossm 사용하기
gossm start(or) 프로파일(scbyun) 설정
gossm start --profile scbyun- Choose a region in AWS: [Use arrows to move, type to filter]
? Choose a region in AWS: ap-northeast-2
region (ap-northeast-2)- Choose a target in AWS: [Use arrows to move, type to filter]
? Choose a target in AWS: dev-web-01 (i-051b9)
[start-session] region: ap-northeast-2, target: i-051b9>gossm start --profile scbyun
? Choose a region in AWS: ap-northeast-2
region (ap-northeast-2)
? Choose a target in AWS: dev-web-01 (i-051b9)
[start-session] region: ap-northeast-2, target: i-051b9
Starting session with SessionId: user@scbyun.com-04bc
sh-4.2$ id
uid=5001(ssm-user) gid=5001(ssm-user) groups=5001(ssm-user)
sh-4.2$ sudo su -
Last login: Mon Feb 6 09:36:21 KST 2023 on pts/0
root@dev-web-01:~$gossm 이용한 ssh 접속 방법
gossm ssh -e '-i key.pem user@server-domain'- 안되네!
gossm 이용하여 private rds 인스턴스에 접속하는 방법
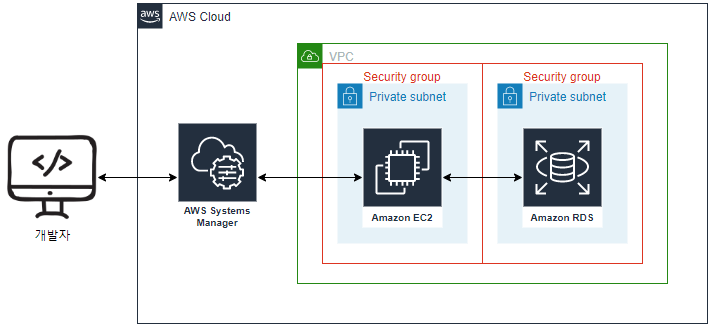
private rds 인스턴스로 3306 포트가 열려 있는지 확인 - FAIL
>tcping tdb.cluster-czglu.ap-northeast-2.rds.amazonaws.com 3306
Probing 10.200.13.4:3306/tcp - No response - time=2008.695ms
Probing 10.200.13.4:3306/tcp - No response - time=2013.239ms
Probing 10.200.13.4:3306/tcp - No response - time=2014.685ms
Probing 10.200.13.4:3306/tcp - No response - time=2001.081ms
Ping statistics for 10.200.13.4:3306
4 probes sent.
0 successful, 4 failed. (100.00% fail)
Was unable to connect, cannot provide trip statistics.gossm fwdrem 명령
gossm fwdrem- Choose a region in AWS :
- Choose a target in AWS :
- Remote port to access :
- Local port number to forward :
- Type your host address you want to forward to :
>gossm fwdrem -p scbyun
? Choose a region in AWS: ap-northeast-2
region (ap-northeast-2)
? Choose a target in AWS: dev-web-01 (i-051b9)
? Remote port to access: 3306
? Remote port to access: 3306
? Local port number to forward: 3306
? Local port number to forward: 3306
? Type your host address you want to forward to: tdb.cluster-czglu.ap-northeast-2.rds.amazonaws.com
? Type your host address you want to forward to: tdb.cluster-czglu.ap-northeast-2.rds.amazonaws.com
[start-port-forwarding 3306 -> 3306] region: ap-northeast-2, target: i-051b9
Starting session with SessionId: user@scbyun.com-03d4
Port 3306 opened for sessionId user@scbyun.com-03d4.
Waiting for connections...private rds 인스턴스로 3306 포트가 열려 있는지 확인 - OK
tcping tdb.cluster-czglu.ap-northeast-2.rds.amazonaws.com 3306
Probing 10.200.14.187:3306/tcp - Port is open - time=7.268ms
Probing 10.200.14.187:3306/tcp - Port is open - time=8.165ms
Probing 10.200.14.187:3306/tcp - Port is open - time=6.902ms
Probing 10.200.14.187:3306/tcp - Port is open - time=7.732ms
Ping statistics for 10.200.14.187:3306
4 probes sent.
4 successful, 0 failed. (0.00% fail)
Approximate trip times in milli-seconds:
Minimum = 6.902ms, Maximum = 8.165ms, Average = 7.517ms
참고URL
- github(gossm) : https://github.com/gjbae1212/gossm
- gossm download : https://github.com/gjbae1212/gossm/releases
- ubuntu에 ssm agent 설치하기 : https://scbyun.com/1412
- Amazon Linux 2 인스턴스에 SSM Agent(Systems Manager Agent) 업데이트하기 : https://scbyun.com/1509
728x90
반응형
'퍼블릭 클라우드' 카테고리의 다른 글
| Amazon EC2 인스턴스에 Elasticsearch를 설치하는 방법 (0) | 2023.02.16 |
|---|---|
| [aws] Amazon Linux 2 인스턴스에 SSM Agent(Systems Manager Agent) 업데이트하기 (0) | 2023.02.06 |
| [클라우드] 클라우드 서비스 공급자(cloud provider) (0) | 2023.01.17 |
| AWS CodeDeploy 에이전트 설치(codedeploy-agent install) (0) | 2023.01.03 |
| [aws] Amazon ECR(프라이빗 레지스트리) (0) | 2022.12.28 |



