반응형
CentOS 7에서 BIND를 사용하여 DNS 포워딩을 설정하는 방법(bind dns forwarding)
DNS 포워딩은 하나의 DNS 서버가 다른 DNS 서버로 DNS 쿼리를 전달하는 기술입니다. 이는 네트워크에서 효율적인 DNS 쿼리 처리와 보안을 강화하는 데 사용됩니다.
테스트 환경
$ cat /etc/redhat-release
CentOS Linux release 7.9.2009 (Core)BIND 설치
sudo yum install -y bind bind-utilsBIND(named) 버전 정보 확인
$ named -v
BIND 9.11.4-P2-RedHat-9.11.4-26.P2.el7_9.15 (Extended Support Version) <id:7107deb>BIND9 Forwarding(8.2.16.2. Forwarding)
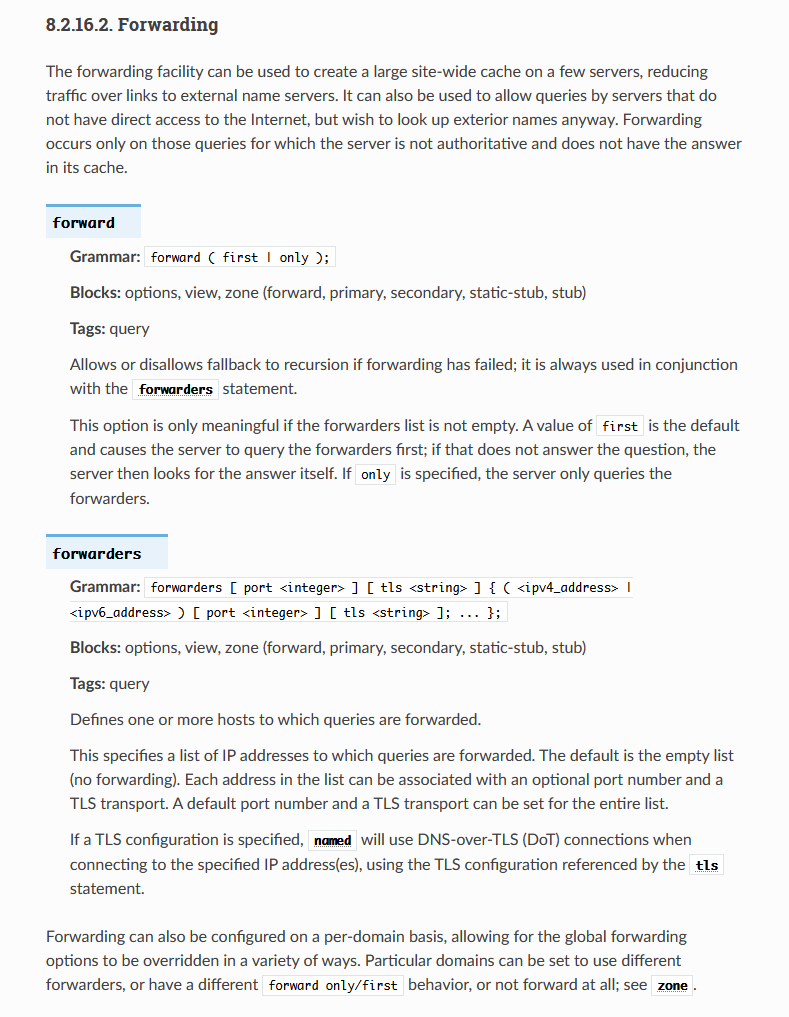
[ forward ( only | first ); ]
[ forwarders { [ ip_addr [port ip_port] ; ... ] }; ]- first : 외부 질의를 할때 우선 포워더를 참조해보고 전부 실패할 경우 직접 처리.
- only : 포워더가 전부 실패해도 직접 처리하지 않음.
옵션 구문
options {
...(생략)
forward only;
// forward to external servers
forwarders {
bastion-ips-go-here;
...(생략)
};도메인 구문
zone zone_name [class] {
type forward;
[ forward (only|first) ; ]
[ forwarders { [ ip_addr [port ip_port] ; ... ] }; ]
};forwarders에 여러 개의 DNS IP를 입력하면 DNS 서버는 이를 1차, 2차 순서로 처리하는 것이 아니라 응답 속도가 가장 빠른 서버에 질의를 보냅니다.
728x90
DNS 포워딩 설정
named 설정 파일(named.conf)
더보기
---
$ cat /etc/named.conf//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// See the BIND Administrator's Reference Manual (ARM) for details about the
// configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html
options {
listen-on port 53 { 127.0.0.1; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { localhost; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.root.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";---
- allow-query-cache { any; };
- forwarders { 8.8.8.8; 1.1.1.1; };
- forward only;
- recursion yes;
vim /etc/named.conf// named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
version "UNKNOWN";
allow-query { any; };
allow-query-cache { any; };
forwarders { 8.8.8.8; 1.1.1.1; };
forward only;
recursion yes;
recursive-clients 10000;
check-names master ignore;
check-names slave ignore;
check-names response ignore;
zone-statistics yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.root.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
statistics-channels {
inet 192.168.0.62 port 7777 allow { 192.168.0.0/24; };
};
include "/etc/named.root.key";
include "/etc/named.rfc1912.zones";
include "/etc/named.logging.conf";named.rfc1912.zones 파일 편집
더보기
---
$ cat /etc/named.rfc1912.zones// named.rfc1912.zones:
//
// Provided by Red Hat caching-nameserver package
//
// ISC BIND named zone configuration for zones recommended by
// RFC 1912 section 4.1 : localhost TLDs and address zones
// and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt
// (c)2007 R W Franks
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
zone "localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};---
vim /etc/named.rfc1912.zoneszone "." IN {
type hint;
file "named.ca";
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};BIND 구성 파일 검사
named-checkconf -z$ named-checkconf -z
zone localhost/IN: loaded serial 0
zone 1.0.0.127.in-addr.arpa/IN: loaded serial 0BIND 서비스 재시
sudo systemctl restart named
CentOS 7 서버에서 BIND를 사용하여 DNS 포워딩이 설정되었습니다.
728x90
반응형
'네임서버' 카테고리의 다른 글
| BIND에서 .jnl 파일 데이터를 존 파일로 가져오는 방법 (0) | 2013.07.04 |
|---|---|
| BIND DNS에서 TSIG를 설정하는 방법 (0) | 2013.07.04 |
| [네임서버] bind를 사용한 마스터-슬레이브 dns 구성하기 (0) | 2013.07.03 |
| DNS 캐싱(caching) 유형 (0) | 2013.07.02 |
| BIND 관리를 위한 RNDC 설정하는 방법 (0) | 2013.07.02 |