반응형
SSL/TLS 암호화 알고리즘(SSLCipherSuite)을 제외하는 방법
- 취약점 암호 스위트
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_256_GCM_SHA384- Nginx에서 SSLCipherSuite에서 특정 알고리즘을 제외하는 방법
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers 'HIGH:!TLS_RSA_WITH_AES_128_CBC_SHA:!TLS_RSA_WITH_AES_256_CBC_SHA:!TLS_RSA_WITH_AES_128_CBC_SHA256:!TLS_RSA_WITH_AES_256_CBC_SHA256:!TLS_RSA_WITH_AES_128_GCM_SHA256:!TLS_RSA_WITH_AES_256_GCM_SHA384';- Apache에서 SSLCipherSuite에서 특정 알고리즘을 제외하는 방법
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite HIGH:!TLS_RSA_WITH_AES_128_CBC_SHA:!TLS_RSA_WITH_AES_256_CBC_SHA:!TLS_RSA_WITH_AES_128_CBC_SHA256:!TLS_RSA_WITH_AES_256_CBC_SHA256:!TLS_RSA_WITH_AES_128_GCM_SHA256:!TLS_RSA_WITH_AES_256_GCM_SHA384
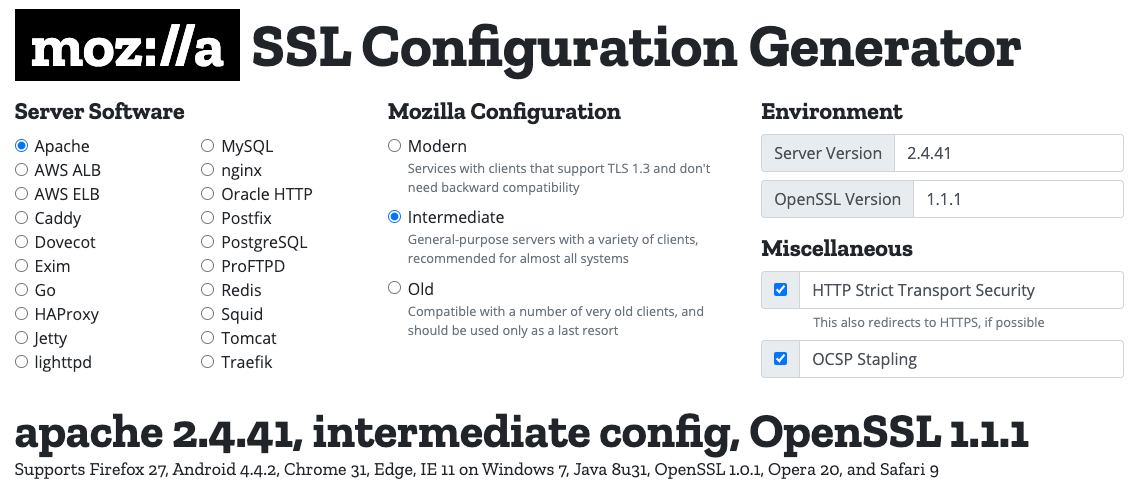
[moz://a SSL] Configuration Generator
# generated 2023-07-04, Mozilla Guideline v5.7, Apache 2.4.41, OpenSSL 1.1.1, intermediate configuration
# https://ssl-config.mozilla.org/#server=apache&version=2.4.41&config=intermediate&openssl=1.1.1&guideline=5.7
# this configuration requires mod_ssl, mod_socache_shmcb, mod_rewrite, and mod_headers
<VirtualHost *:80>
RewriteEngine On
RewriteCond %{REQUEST_URI} !^/\.well\-known/acme\-challenge/
RewriteRule ^(.*)$ https://%{HTTP_HOST}$1 [R=301,L]
</VirtualHost>
<VirtualHost *:443>
SSLEngine on
# curl https://ssl-config.mozilla.org/ffdhe2048.txt >> /path/to/signed_cert_and_intermediate_certs_and_dhparams
SSLCertificateFile /path/to/signed_cert_and_intermediate_certs_and_dhparams
SSLCertificateKeyFile /path/to/private_key
# enable HTTP/2, if available
Protocols h2 http/1.1
# HTTP Strict Transport Security (mod_headers is required) (63072000 seconds)
Header always set Strict-Transport-Security "max-age=63072000"
</VirtualHost>
# intermediate configuration
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305
SSLHonorCipherOrder off
SSLSessionTickets off
SSLUseStapling On
SSLStaplingCache "shmcb:logs/ssl_stapling(32768)"
OpenSSL을 사용하여 웹 사이트가 특정 암호화 알고리즘을 사용하는지 확인하는 방법
echo | openssl s_client -connect <웹사이트 주소>:<포트번호> -cipher <암호화 알고리즘>실제 웹 사이트 주소와 포트 번호를 입력하여 위의 명령어를 실행하고, 각각의 암호화 알고리즘에 대해 확인해보세요.
예를 들어, TLS_RSA_WITH_AES_128_CBC_SHA 암호화 알고리즘을 확인하려면 다음과 같이 명령어를 실행할 수 있습니다.
echo | openssl s_client -connect <웹사이트 주소>:<포트번호> -cipher 'AES128-SHA'
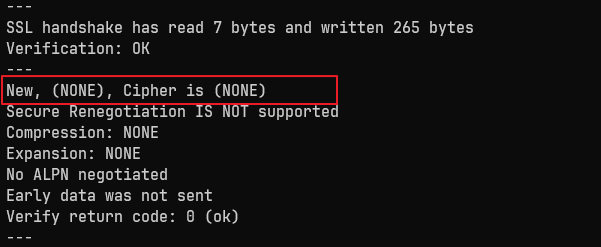
echo | openssl s_client -connect sangchul.kr:443 -cipher 'AES128-SHA' 2>&1 | grep "Cipher is"$ echo | openssl s_client -connect sangchul.kr:443 -cipher 'AES128-SHA' 2>&1 | grep "Cipher is"
New, SSLv3, Cipher is AES128-SHA명령어를 실행하면 해당 암호화 알고리즘을 사용하는지 여부와 함께 SSL/TLS 연결에 대한 정보가 출력됩니다. 출력 결과에서 "Cipher is (NONE)"이라는 메시지가 나오면 해당 암호화 알고리즘을 사용하지 않는 것입니다.

Accepted: "Accepted"는 서버가 클라이언트의 제안을 수락하고 사용할 것을 의미합니다. 핸드셰이크 과정에서 클라이언트가 제안한 암호화 알고리즘, 키 교환 알고리즘 등이 서버에게 수락되었음을 나타냅니다. 이는 클라이언트와 서버 간의 암호화 통신에 사용될 알고리즘과 옵션이 서버 측에서 선택되었음을 의미합니다.
$ sslscan --no-failed sangchul.kr | grep Accepted
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve P-256 DHE 256
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA256 Curve P-256 DHE 256
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA Curve P-256 DHE 256
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA384 Curve P-256 DHE 256
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256
Accepted TLSv1.2 128 bits DHE-RSA-AES128-GCM-SHA256 DHE 2048 bits
Accepted TLSv1.2 128 bits DHE-RSA-AES128-SHA256 DHE 2048 bits
Accepted TLSv1.2 128 bits DHE-RSA-AES128-SHA DHE 2048 bits
Accepted TLSv1.2 256 bits DHE-RSA-AES256-GCM-SHA384 DHE 2048 bits
Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA256 DHE 2048 bits
Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA DHE 2048 bits
Accepted TLSv1.2 128 bits DHE-RSA-CAMELLIA128-SHA DHE 2048 bits
Accepted TLSv1.2 256 bits DHE-RSA-CAMELLIA256-SHA DHE 2048 bits
Accepted TLSv1.2 256 bits AES256-GCM-SHA384
Accepted TLSv1.2 256 bits AES256-SHA256
Accepted TLSv1.2 256 bits AES256-SHA
Accepted TLSv1.2 256 bits CAMELLIA256-SHA
Accepted TLSv1.2 128 bits AES128-GCM-SHA256
Accepted TLSv1.2 128 bits AES128-SHA256
Accepted TLSv1.2 128 bits AES128-SHA
Accepted TLSv1.2 128 bits CAMELLIA128-SHA
Accepted TLSv1.2 ?? bits TLS_RSA_WITH_SEED_CBC_SHA
Accepted TLSv1.2 112 bits TLS_RSA_WITH_3DES_EDE_CBC_SHA
Accepted TLSv1.2 128 bits TLS_RSA_WITH_IDEA_CBC_SHA
Accepted TLSv1.1 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256
Accepted TLSv1.1 128 bits DHE-RSA-AES128-SHA DHE 2048 bits
Accepted TLSv1.1 256 bits DHE-RSA-AES256-SHA DHE 2048 bits
Accepted TLSv1.1 128 bits DHE-RSA-CAMELLIA128-SHA DHE 2048 bits
Accepted TLSv1.1 256 bits DHE-RSA-CAMELLIA256-SHA DHE 2048 bits
Accepted TLSv1.1 256 bits AES256-SHA
Accepted TLSv1.1 256 bits CAMELLIA256-SHA
Accepted TLSv1.1 128 bits AES128-SHA
Accepted TLSv1.1 128 bits CAMELLIA128-SHA
Accepted TLSv1.1 ?? bits TLS_RSA_WITH_SEED_CBC_SHA
Accepted TLSv1.1 112 bits TLS_RSA_WITH_3DES_EDE_CBC_SHA
Accepted TLSv1.1 128 bits TLS_RSA_WITH_IDEA_CBC_SHA
Accepted TLSv1.0 256 bits ECDHE-RSA-AES256-SHA Curve P-256 DHE 256
Accepted TLSv1.0 128 bits DHE-RSA-AES128-SHA DHE 2048 bits
Accepted TLSv1.0 256 bits DHE-RSA-AES256-SHA DHE 2048 bits
Accepted TLSv1.0 128 bits DHE-RSA-CAMELLIA128-SHA DHE 2048 bits
Accepted TLSv1.0 256 bits DHE-RSA-CAMELLIA256-SHA DHE 2048 bits
Accepted TLSv1.0 256 bits AES256-SHA
Accepted TLSv1.0 256 bits CAMELLIA256-SHA
Accepted TLSv1.0 128 bits AES128-SHA
Accepted TLSv1.0 128 bits CAMELLIA128-SHA
Accepted TLSv1.0 ?? bits TLS_RSA_WITH_SEED_CBC_SHA
Accepted TLSv1.0 112 bits TLS_RSA_WITH_3DES_EDE_CBC_SHA
Accepted TLSv1.0 128 bits TLS_RSA_WITH_IDEA_CBC_SHA
$sslscan --no-failed www.sangchul.kr | grep Accepted
Accepted TLSv1.3 256 bits TLS_AES_256_GCM_SHA384 Curve 25519 DHE 253
Accepted TLSv1.3 256 bits TLS_CHACHA20_POLY1305_SHA256 Curve 25519 DHE 253
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve 25519 DHE 253
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA Curve 25519 DHE 253
Accepted TLSv1.2 128 bits AES128-GCM-SHA256
Accepted TLSv1.2 128 bits AES128-SHA
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-GCM-SHA384 Curve 25519 DHE 253
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA Curve 25519 DHE 253
Accepted TLSv1.2 256 bits AES256-GCM-SHA384
Accepted TLSv1.2 256 bits AES256-SHA
Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-SHA256 Curve 25519 DHE 253
Accepted TLSv1.2 128 bits AES128-SHA256
Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA384 Curve 25519 DHE 253
Accepted TLSv1.2 256 bits AES256-SHA256
Accepted TLSv1.1 128 bits AES128-SHA
Accepted TLSv1.1 256 bits ECDHE-RSA-AES256-SHA Curve 25519 DHE 253
Accepted TLSv1.1 256 bits AES256-SHA
Accepted TLSv1.0 128 bits AES128-SHA
Accepted TLSv1.0 256 bits ECDHE-RSA-AES256-SHA Curve 25519 DHE 253
Accepted TLSv1.0 256 bits AES256-SHA
Accepted TLSv1.0 112 bits TLS_RSA_WITH_3DES_EDE_CBC_SHA
$ sslscan --show-ciphers www.sangchul.kr
참고URL
- 암호 스위트 이름(cipher suite names) : https://www.openssl.org/docs/man1.1.1/man1/ciphers.html
728x90
반응형
'리눅스' 카테고리의 다른 글
| Ubuntu에 최신 버전의 OpenSSL을 컴파일하고 설치하는 방법 (0) | 2023.07.06 |
|---|---|
| 우분투에서 UTF-8 언어셋으로 변경하는 방법 (0) | 2023.07.05 |
| 우분투에 sslscan을 설치하고 사용하는 방법 (0) | 2023.07.05 |
| docker inspect 명령어 (0) | 2023.07.04 |
| Ubuntu에서 NTP 서버를 구성하는 방법 (0) | 2023.07.02 |