리눅스
취약점을 방지하기 위한 보안 HTTP 헤더를 설정하기
변군이글루
2020. 10. 21. 14:37
반응형
취약점을 방지하기 위한 보안 HTTP 헤더를 설정하기
X-Content-Type-Options
###Apache
Header set X-Content-Type-Options nosniff
###Nginx
add_header X-Content-Type-Options nosniff;
X-XSS-Protection
###Apache
Header set X-XSS-Protection "1; mode=block"
###Nginx
add_header X-XSS-Protection "1; mode=block";X-Frame-Options
###Apache
Header always append X-Frame-Options DENY
###Nginx
add_header X-Frame-Options “DENY”;HTTP Strict Transport Securit
###Apache
Header set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"
###Nginx
add_header Strict-Transport-Security 'max-age=31536000; includeSubDomains; preload';https://geekflare.com/http-header-implementation/
How to Implement Security HTTP Headers to Prevent Vulnerabilities? - Geekflare
Do you know most of the security vulnerabilities can be fixed by implementing necessary headers in the response header? Security is as essential as
geekflare.com
apache 설정 및 적용 내용 확인
httpd.conf 편집
$ vim /usr/local/apache2/conf/httpd.conf
...
Header always set X-Content-Type-Options "nosniff"
Header set X-XSS-Protection "1; mode=block"
Header always append X-Frame-Options DENY
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"웹 브라우저 개발툴로 확인
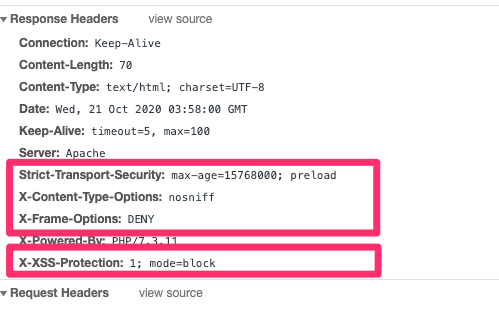
curl 툴로 확인
curl -I http://localhost$ curl -I http://localhost
HTTP/1.1 200 OK
Date: Wed, 21 Oct 2020 05:41:26 GMT
Server: Apache
X-Content-Type-Options: nosniff
X-Frame-Options: DENY
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
X-XSS-Protection: 1; mode=block
Content-Type: text/html; charset=UTF-8
728x90
반응형